[
{
"code": 13014,
"msg": "User does not have credentials to access privilege cluster.bucket[mynewbucket].data.docs!read. Add role Data Reader[mynewbucket] to allow the query to run."
}
]Posts tagged with 'c'
Eric Maxwell talks Realm's NoSQL database for mobile.
Show Notes:
- Realm.io
- The NoSQL Database Podcast
- Eric Maxwell's episode will be published in June
- Subscribe to The NoSQL Database Podcast on iTunes, or check out the podcast on LibSyn
- There was some discussion of the difference between an object database and a document database
- Realm on Github
- Eric was kind enough to share his email address in the podcast.
- #Hashtag Comedy Troupe in Columbus, Ohio
Want to be on the next episode? You can! All you need is the willingness to talk about something technical.
Theme music is "Crosscutting Concerns" by The Dirty Truckers, check out their music on Amazon or iTunes.
Arthur Doler talks about retrospectives and how to make them better.
Note that this was recording at the Indy.Code() conference in a hallway, so the audio may be a bit noisier than usual.
Also, SPECIAL THANKS to the great David Giard (who has been on the show before: Episode 6 and Episode 15, and he's also the host of the excellent Techology and Friends show, of which my podcast is a pale imitation) who gave me some new podcasting equipment that I used in this episode. I am extremely grateful, but I'm still trying to figure out how best to use this equipment (which may be obvious in this episode).
Show Notes:
- Book: Thinking, Fast and Slow by Daniel Kahneman
- Hidden Brain by Shankar Vedantam
- Hidden Brain podcast on NPR
- Hidden Brain book
- Book: You Are No So Smart by David McRaney
- Arthur was kind enough to give his email address in the podcast if you want to contact him.
Want to be on the next episode? You can! All you need is the willingness to talk about something technical.
Theme music is "Crosscutting Concerns" by The Dirty Truckers, check out their music on Amazon or iTunes.
This is a repost that originally appeared on the Couchbase Blog: Authorization and Authentication with RBAC (Part 2).
Authorization and authentication are important to Couchbase. In March, I blogged about some of the new Role Based Access Control (RBAC) that we are showing in the Couchbase Server 5.0 Developer Builds. This month, I’d like to go into a little more detail now that the April Couchbase Server 5.0 Developer Build is available (make sure to click the "Developer" tab).
Authentication and authorization
In past version of Couchbase, buckets were secured by a password. In 5.0, bucket passwords for authorization are gone. You can no longer create a "bucket password" for authorization. Instead, you must create one (or more) users that have varying levels of authorization for that bucket. Notice that there is no "password" field anymore (not even in the "Advance bucket settings":
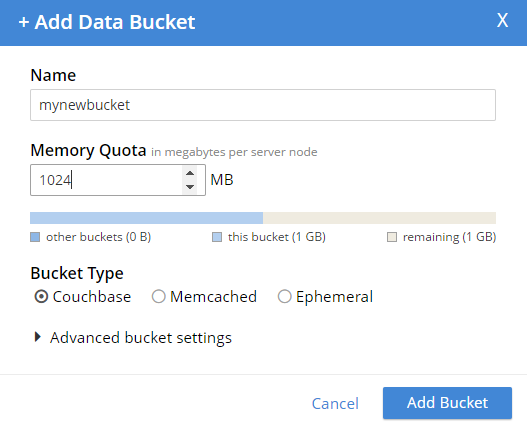
So now, you no longer have to hand out a password that gives complete access to a bucket. You can fine-tune bucket authorization, and give out multiple sets of credentials with varying levels of access. This will help you tighten up security, and reduce your exposure.
Note: The administrator user still exists, and has permission to do everything. So I can still run N1QL queries (for instance) on that bucket while logged in as an administrator account. However, this is not the account you should be using from your clients.
Creating an authorized user
To create a new user, you must be logged in as an administrator (or as a user that has an Admin role). Go to the "Security" tab, and you’ll be able to see a list of users, and be able to add new ones.
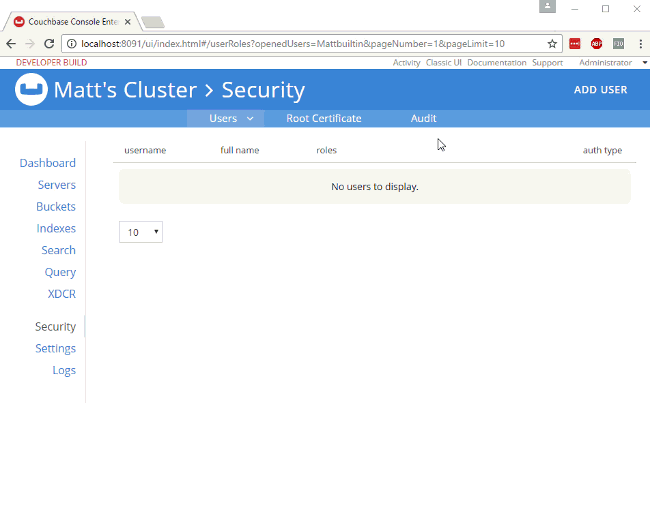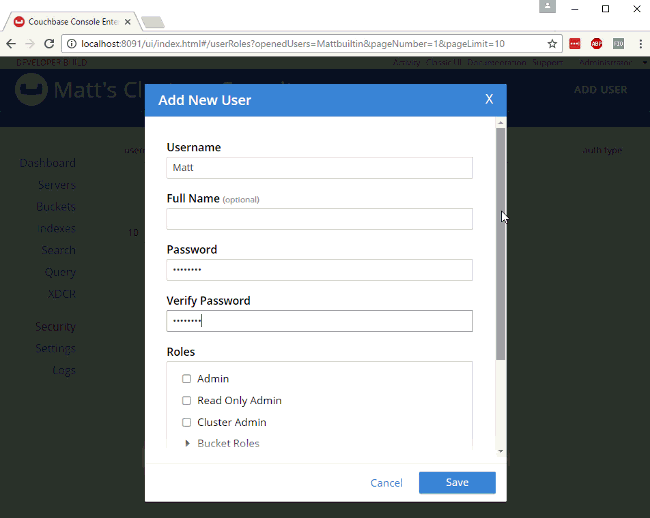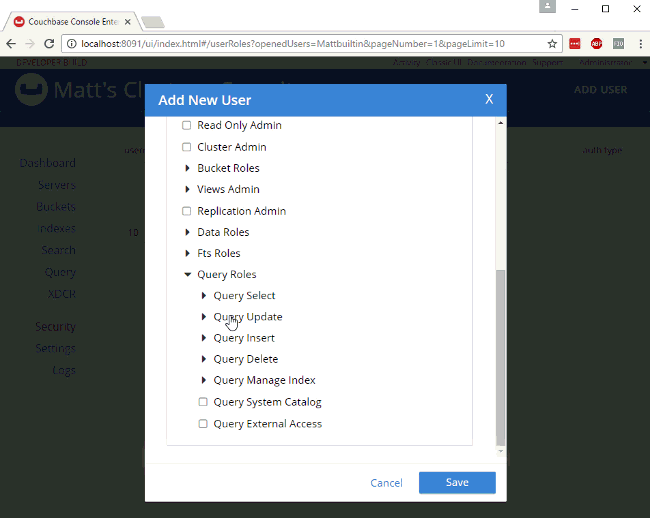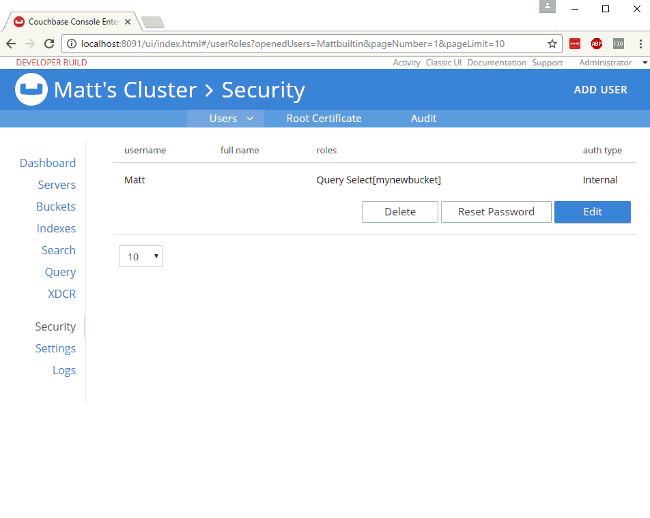
Create a new user by clicking "ADD USER". Enter the information for the user. You may want to create a user for a person (e.g. "Matt"), or you may want to create a user for a service (e.g. "MyAspNetApplication"). Make sure to enter a strong password, and then select the appropriate roles for the user you want to create.
For example, let’s create a user "Matt" that only has access to run SELECT queries on the bucket I just created. In "Roles", I expand "Query Roles", then "Query Select", and check the box for "mynewbucket", and then "Save" to finalize the user.
Authorization in action
When I log out of the administrator account, and log back in as "Matt", I can see that the authorization level I have is severely restricted. Only "Dashboard", "Servers", "Settings", and "Query" are visible. If I go to "Query" I can execute SELECT 1;
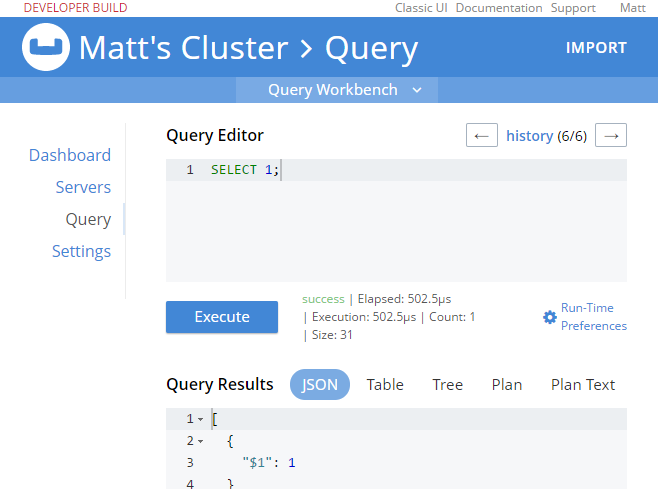
If I try something more complex, like SELECT COUNT(1) FROM mynewbucket, I’ll get an error message like:
So, it looks like I have the correct authentication to log in, and I have the correct authorization to execute a SELECT, but I don’t have the correct authorization to actually read the data. I’ll go back in as admin, and add Data Reader authorization.
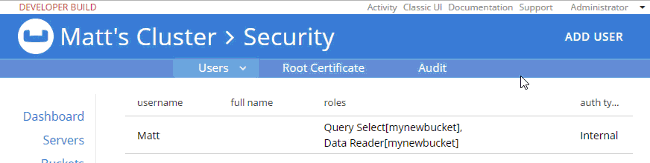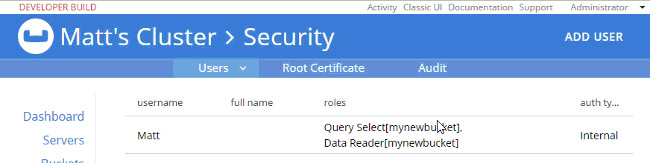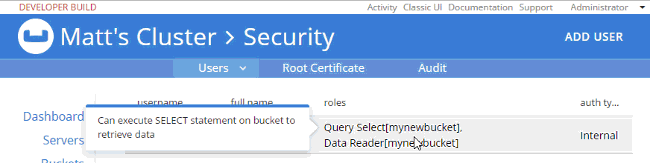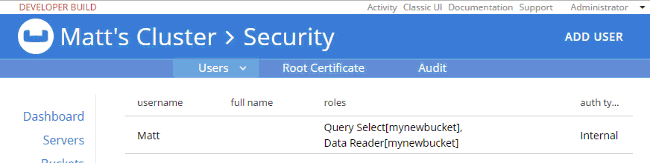
At this point, when I login with "Matt", SELECT COUNT(1) FROM mynewbucket; will work. If you are following along, try SELECT * FROM mynewbucket;. You’ll get an error message that no index is available. But, if you try to CREATE INDEX you’ll need another permission to do that. You get the idea.
New N1QL functionality
There’s some new N1QL functionality to go along with the new authentication and authorization features.
GRANT and REVOKE ROLE
You can grant and revoke roles with N1QL commands. You need Admin access to do this.
Here’s a quick example of granting SELECT query authorization to a user named "Matt" on a bucket called "mynewbucket":
GRANT ROLE query_select(`mynewbucket) TO Matt;`
And likewise, you can REVOKE a role doing something similar:
REVOKE ROLE query_select(`mynewbucket) FROM Matt;`
Creating users with REST
There is no way (currently) to create users with N1QL, but you can use the REST API to do this. Full documentation is coming later, but here’s how you can create a user with the REST API:
-
PUT to the
/settings/rbac/users/builtin/<username>endpoint. -
Use admin credentials for this endpoint (e.g. Administrator:password with basic auth)
-
The body should contain:
-
roles=<role1,role2,…,roleN>
-
password=<password>
-
Below is an example. You can use cURL, Postman, Fiddler, or whatever your favorite tool is to make the request.
Headers: Content-Type: application/x-www-form-urlencoded Authorization: Basic QWRtaW5pc3RyYXRvcjpwYXNzd29yZA==
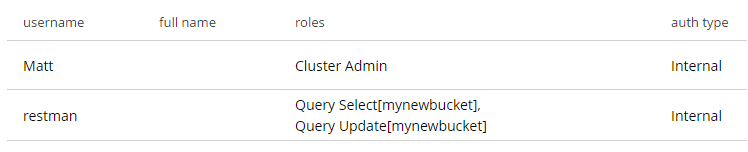
Body: roles=query_select[mynewbucket],query_update[mynewbucket]&password=password
The above assumes that you have an admin user/password of Administrator/password (hence the basic auth token of QWRtaW5pc3RyYXRvcjpwYXNzd29yZA==).
After executing that, you’ll see a new user named "restman" with the two specified permissions.
Wait, there’s more!
The RBAC system is far too rich to cover in a single blog post, and full documentation is on its way. In the meantime, here are some details that might help you get started with the preview:
-
You may have noticed the
alloption in the screenshots above. You can give a user roles on a bucket-by-bucket basis, or you can give permission to all buckets (even buckets that haven’t been created yet. -
I covered FTS permissions in the previous blog post, but there are permissions that cover just about everything: views, bucket administration, backup, monitoring, DCP, indexes, etc.
-
You can’t create buckets with a password anymore. The equivalent is to instead create a user with the name as the bucket, and give it authorization to a role called "Bucket Full Access". This will be useful for upgrading and transitioning purposes.
We still want your feedback!
Stay tuned to the Couchbase Blog for information about what’s coming in the next developer build.
Interested in trying out some of these new features? Download Couchbase Server 5.0 April 2017 Developer Build today!
The 5.0 release is fast approaching, but we still want your feedback!
Bugs: If you find a bug (something that is broken or doesn’t work how you’d expect), please file an issue in our JIRA system at issues.couchbase.com or submit a question on the Couchbase Forums. Or, contact me with a description of the issue. I would be happy to help you or submit the bug for you (my Couchbase handlers let me take selfies on our cartoonishly big couch when I submit good bugs).
Feedback: Let me know what you think. Something you don’t like? Something you really like? Something missing? Now you can give feedback directly from within the Couchbase Web Console. Look for the ![]() icon at the bottom right of the screen.
icon at the bottom right of the screen.
In some cases, it may be tricky to decide if your feedback is a bug or a suggestion. Use your best judgement, or again, feel free to contact me for help. I want to hear from you. The best way to contact me is either Twitter @mgroves or email me matthew.groves@couchbase.com.
Eric Potter talks about the new pattern matching features in C# 7.
Note that this was recording at the Indy.Code() conference in a hallway, so the audio may be a bit noisier than usual. At one point a firetruck drove by.
Show Notes:
- Edsger Dijkstra lays out the three main control structures (I believe) in Structured Programming (with C.A.R. Hoare)
- Aptera blog
- Eric Potter's blog Humble Toolsmith
- What's New in C# 7 blog post by Mads Torgersen
Want to be on the next episode? You can! All you need is the willingness to talk about something technical.
Theme music is "Crosscutting Concerns" by The Dirty Truckers, check out their music on Amazon or iTunes.
Matthew Revell talks about creating and running developer conferences.
Show Notes:
- Conferences that Matthew mentioned:
- White October Events
- Blog: DevRel
Want to be on the next episode? You can! All you need is the willingness to talk about something technical.
Theme music is "Crosscutting Concerns" by The Dirty Truckers, check out their music on Amazon or iTunes.




